Console - Content Storage
This section describes how to run and manage the network and configuration services in a single Swarm cluster using the Content Storage tab options in the CSN console. The CSN currently provides network and configuration services for a single Swarm cluster.
Note
CSN 8.3 includes both the Swarm Storage UI and /wiki/spaces/DOCS/pages/2443813497, which populates the UI with usage data. With these new cluster reporting mechanisms, the legacy Reporter tab has been removed.
Configuration (storage cluster)
The CSN will automatically configure Swarm in multi-server mode to take advantage of all available CPU cores. The number of Swarm processes assigned to each node is dynamically determined based on system information provided by the node when it requests its network boot configuration. IP addresses are statically assigned to each node and then maintained by a CSN process that pings each node every 5 minutes. If a node has not responded to a ping in 72 hours, its IP address will be released and a new one assigned if the node should come back online at a later time. The maximum number of allowed processes per node, the interval at which nodes are pinged (default 5 minutes) and the length of time the CSN waits before releasing the IP address for a node that has not responded (default 72 hours) are all configurable. Please contact your support representative for instructions on modifying these parameters.
Note: When replacing older hardware, particularly if running with a small network, you may need to either work with your support representative to decrease the IP release timeout or bring new nodes online one at a time to ensure you have enough IP addresses available until the older nodes have released their IPs after the timeout period.
A list of all IP address assignments and the associated node's MAC address can be obtained by running the following command line script:
/opt/caringo/csn/bin/ip-assignments
MAC addresses will appear multiple times in the output if the nodes have enough CPU cores to support more than one Swarm process. The script will not return any results if no storage nodes have been booted yet.
By default, the configuration passed to Swarm nodes during the netboot process will specify that all network interfaces be bonded using Balance-ALB bonding.
Booting Nodes
| Dual-network | Upon boot of a new node onto the internal network via network boot, a CSN configured in dual-network mode will automatically provide the needed configuration and software. With subsequent boots of a previously known node on the network, the CSN will recognize the Swarm node and use its previously assigned configuration to boot the node. For an additional level of control over what servers get booted as Swarm nodes in a dual-network configuration, administrators may choose to enable netboot protection as described below. To enable netboot protection, click the 'Enable Protection' button at the bottom of the Content Storage > Netboot Protect page of the CSN console. |
|---|---|
| Single-network | Once a server has its MAC addresses listed on the Content Storage > Netboot Protect page, you may boot the server and the CSN will provide the needed configuration and software. If your single-network environment is controlled to the point where booting unknown nodes is not a concern, you may alternately disable netboot protection by clicking the Disable Protection button. This will allow any server that requests a netboot image to be formatted as a Swarm node without having its MAC addresses listed. Important Unlike a dual-network configuration, where the CSN is the network gateway for the Swarm nodes, a single-network configuration has the Swarm nodes using the same gateway as the CSN. |
Updating Configuration Settings
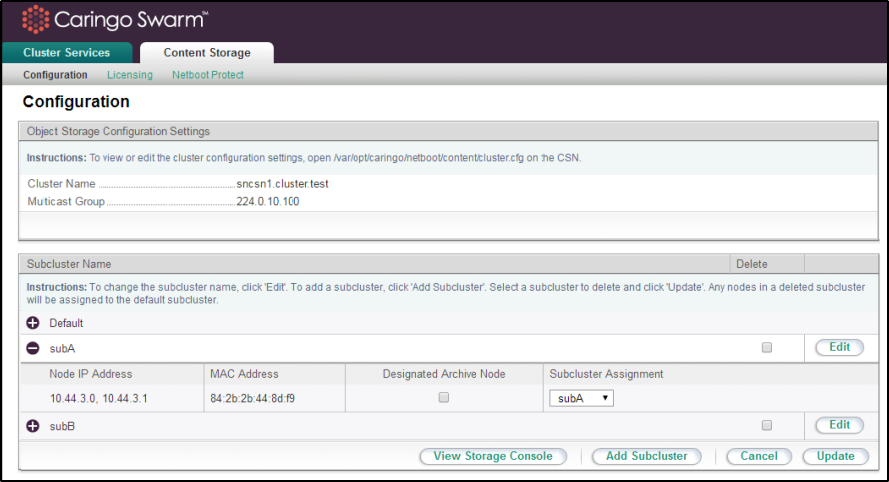
In addition to the default network configuration information gathered from the initial configuration of the CSN, the CSN Console displays a few configuration parameters from the Content Storage > Configuration page.
Field | Description |
|---|---|
Cluster Name | The read-only name of the cluster that was specified during the initial network configuration process. |
Multicast Group | The multicast address for the cluster. It must be a Class D IP address in the range 224.0.0.0 - 239.255.255.255. |
See Persisted Settings (SNMP), which describes runtime settings that must be changed via SNMP.
To make changes to boot-time settings on the CSN, edit the configuration file located at /var/opt/caringo/netboot/content/cluster.cfg. Any boot- time configuration changes, both cluster and node level, will not take effect until the cluster is rebooted to pick up the new configuration. Note that manually configuring node IPs is not supported as the CSN expects ownership of the IP address space for Swarm nodes both when assigning IPs for new nodes and when gathering data for reporting.
The Swarm configuration page allows editing of a few node-level parameters. All nodes that have been network booted by the CSN will be included in the listed nodes with their MAC address and IP address. Any nodes that previously booted from the CSN but have since expired will not be included. For multi-process servers, each row in the interface will contain multiple IP addresses that identify the different virtual nodes in the server. These virtual nodes cannot have their subcluster or archive node status set independently. The nodes will be listed underneath their assigned subcluster. If no subcluster has been assigned, nodes will be listed in the 'Default' subcluster.
From the node list, it is possible to set the subcluster for an individual node, as well as whether or not it should be set as an archive node. See the Node Configuration for usage information of these configuration parameters. Prior to assigning subclusters to a node, the list of allowed subclusters must be created using the 'Add Subcluster' button to ensure consistency. Subcluster names may only contain letters, numbers, spaces, and underscores. If a subcluster is edited, all corresponding entries for each related node will also be updated.
Caution
On the Content Storage > Configuration tab, if you Edit and remove the Subcluster Assignment, doing so creates an invalid config parameter that will prevent the unassigned node from booting.
Using the Swarm Admin Console
Swarm includes its own administrative console, which can be reached directly from the external network by entering the following address:
http://{CSN·external·IP}:8090/services/storage/The Swarm admin console may also be accessed by clicking the View Storage Console button on any page of the Content Storage tab page of the CSN Console.
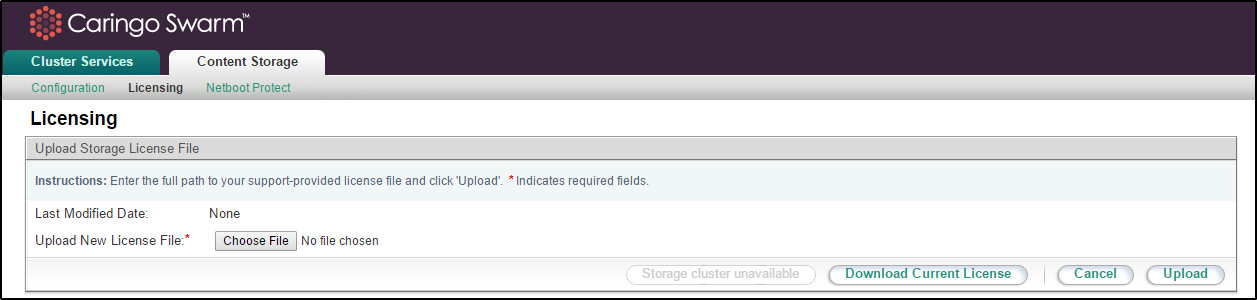
Licensing (upload license file)
Use the Licensing tab to update your Swarm license file whenever there are changes:
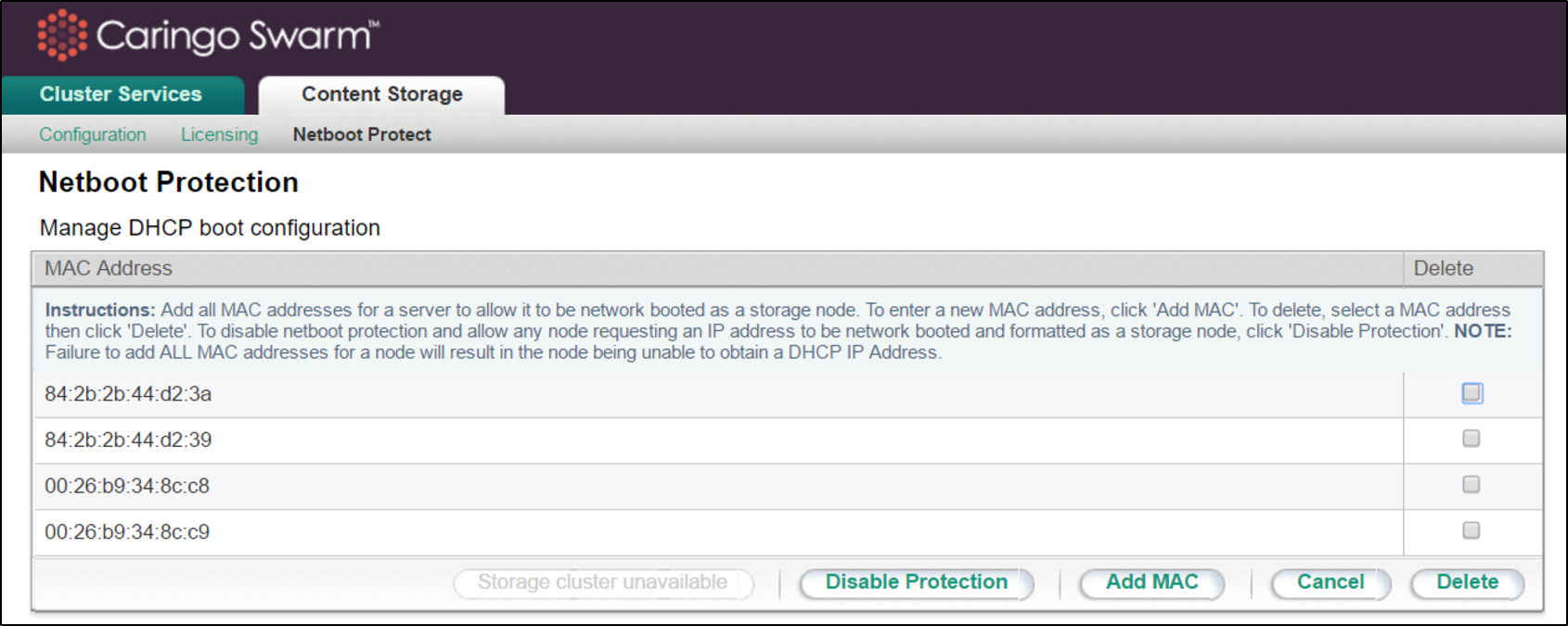
Netboot Protect (from unintended formatting)
To prevent the unintended formatting of servers not intended to be Swarm nodes when netboot protection is enabled (default for single network installations), you must first add all MAC addresses for any server you do intend to use as a Swarm node on the Content Storage > Netboot Protect page of the CSN console.
Due to NIC bonding, entering a single MAC address for a server is not sufficient; all MAC addresses must be included. If you are unsure how to obtain the MAC addresses for the server, try booting the storage nodes and then check the /var/log/messages log to see what MAC addresses requested an IP address. You can search for related DHCP messages in that log with a command similar to the following:
[root@csninternalnic ~]# grep 'DHCPDISCOVER' /var/log/messages
A matching log message might look like the following, where e0:91:f5:08:6b:17 is the MAC address of a node requesting an IP address:
127.0.0.1 <27>Oct 9 16:21:05 dhcpd: DHCPDISCOVER from e0:91:f5:08:6b:17 via bond0: network 10.44.0.0/16: no free leases
The 'no free leases' error message is an indication that a node has asked for a DHCP address but it is not included in the netboot protection page so an IP Address is not granted. This method of finding MAC addresses may result in extra results if there are servers that are not Swarm nodes mistakenly asking the CSN's DHCP server for an IP Address.
Warning
© DataCore Software Corporation. · https://www.datacore.com · All rights reserved.